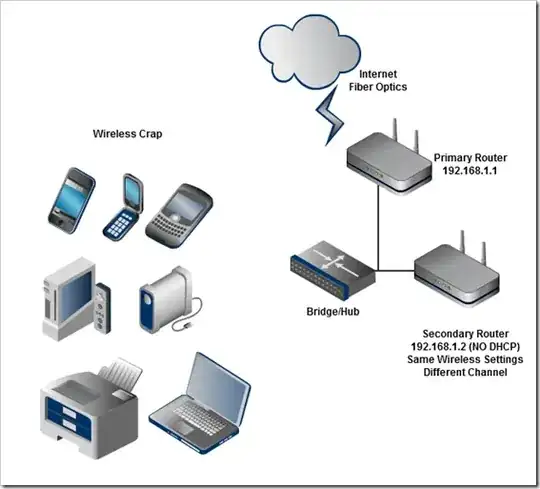
I'm using Firefox Beta 103 (tried with stable and nightly too), enabled Cloudflare DNS over HTTPS in settings:
then enabled these:
network.dns.echconfig.enabled
and
network.dns.http3_echconfig.enabled
but when visiting this website https://www.cloudflare.com/ssl/encrypted-sni/#results
I get this result
so what am I missing here?