We have a machine that we are trying to limit bandwidth to, using pfSense. This is because the machine is using 80% of our link:
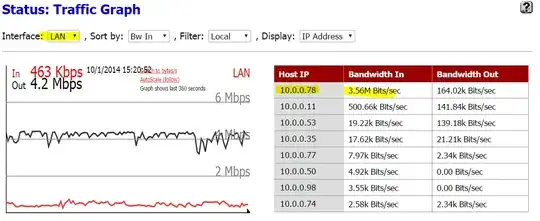
Another brute-force method of limiting bandwidth to an IP address is simply to block it. So we updated a rule to indicate that it should be a Block rule:
We also created another rule, randomly picking other options to try to block 10.0.0.78 from talking to the Internet:
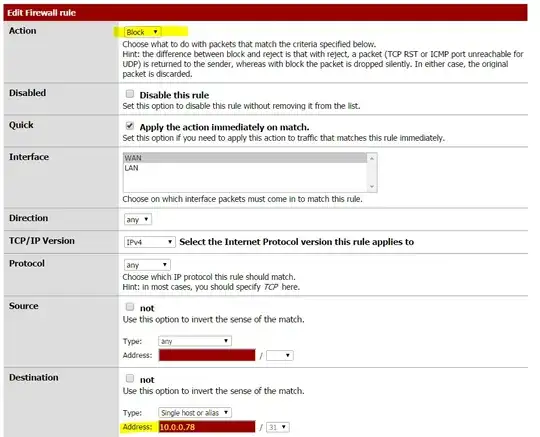
Yet there it is, still consuming the majority of the bandwidth:

And when you log into the machine, uTorrent is still merrily downloading data.
How do you block a computer, by IP address, in pfSense?