Based on the structure of the udp packet, you should cut the tcpdump output from a specific location, instead of looking for a certain character, which could also change:
sudo tcpdump -Aq -i lo udp port 1234 | cut -c29-
For example, sending a udp packet with netcat:
echo "HELLO" | netcat -4u -w1 localhost 1234
this is my tcpdump output (in hex and ascii ):
sudo tcpdump -X -i lo udp port 1234
12:35:10.672236 IP localhost.36898 > localhost.1234: UDP, length 6
0x0000: 4500 0022 ab0e 4000 4011 91ba 7f00 0001 E.."..@.@.......
0x0010: 7f00 0001 9022 04d2 000e fe21 4845 4c4c .....".....!HELL
0x0020: 4f0a O.
but, sending another string, like:
echo "HELLOS" | netcat -4u -w1 localhost 1234
this is the output:
12:50:01.987211 IP localhost.45180 > localhost.1234: UDP, length 7
0x0000: 4500 0023 3873 4000 4011 0455 7f00 0001 E..#8s@.@..U....
0x0010: 7f00 0001 b07c 04d2 000f fe22 4845 4c4c .....|....."HELL
0x0020: 4f53 0a OS.
the character before the string "HELLOS" is changed, because the 2 byte preceding the date section are related to the udp checksum, and then change according to the packet sent.
whireshark screenshot:
IP:
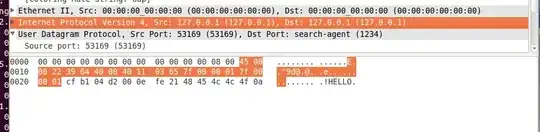
UDP packet:
 and 2 byte checksum:
and 2 byte checksum:


 and 2 byte checksum:
and 2 byte checksum: