Many articles only contain a phrasing like
A miner
Asolves the hash problem and gives the result to the network to check. Once a majority of the network confirms,Agets the reward.
But how does one protect his effort from being stolen? As I think:
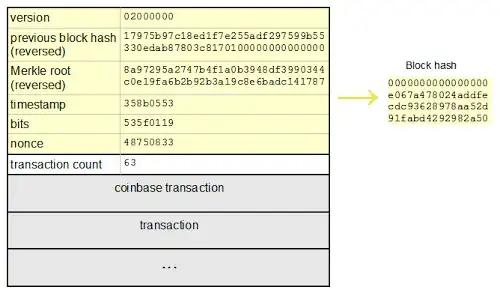
Asolved the problem, soAget original stringSwhich could be hashed to target hashH.Asends his result to the network (some other miners) intending to get the reward.- Other nodes (miners) need to hash
Sand check whether the result equal toHto determine whetherAis right or not. (So I think here one can getSandH) - But
BnearA, he getA's works, so he get theSandH. Then he can construct a new result send to others, claim thatBsolved the problem - If
Bcan spread his result faster thanA, he gets the reward.
I have seen Can a miner steal another one's block? , in which @Highly Irregular says
The block that Alice mined includes the mining rewards going to Alice's address. If Eve alters the block data to output the rewards to her own receiving address, then the nonce (and other variable values, I think "extranonce" and timestamp) that Alice used to solve the block will almost certainly no longer solve the block.
But he didn't tell how in detail.
@Stéphane Gimenez gave the normal steps of mining here, in which I didn't see a measure to prevent B from stealing the block from A (or how to validate the result is originally calculated by A).