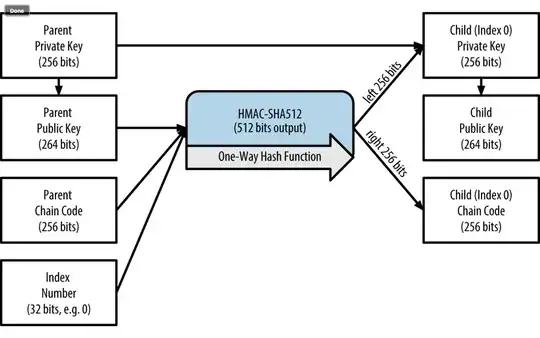
I am a newbie and start exploring from the 'Mastering Bitcoin' book. The figure below to me is a little inaccurate, I think the arrow from HMAC-SHA256 should point right to the child public key. Am I right??
- 113
- 3
2 Answers
I think the arrow from HMAC-SHA256 should point right to the child public key. Am I right??
No, there are 3 derivation functions defined in BIP32 - Hierarchical Deterministic Wallets
- Private parent key → private child key
- Public parent key → public child key
- Private parent key → public child key
The diagram above illustrates
1. Private parent key → private child key
Perhaps you're confusing this for 2. Public parent key → public child key. Another potential confusion is that this is not for a hardened child key but a normal child key, which uses the parent public key point(kpar), combined with the parent chain code cpar and the index i. These are combined and hashed to I as follows:
I = HMAC-SHA512(Key = cpar, Data = serP(point(kpar)) || ser32(i))
I is split as shown in the diagram, where the left 256 bits IL are combined with the parent private key kpar to produce the child private key ki:
ki = parse256(IL) + kpar (mod n)
IR is the new child's chain code at that index i, and the child public key is then calculated like normal using elliptic curve secp256k1 from the child private key itself.
- 7,278
- 1
- 11
- 32
-
so if this figure is meant to to demonstrate how to “Extending a parent public key to create a child public key” it would be wrong, right? sorry I didn't post with the note included – Phạm Huy Phát Aug 12 '18 at 04:27
-
It would be wrong in that case – JBaczuk Aug 12 '18 at 04:39
I have to agree, https://github.com/bitcoinbook/bitcoinbook/blob/develop/ch05.asciidoc still needs a little work.
Here is my perspective, the application of BIP32 Deterministic Key Generator and bitcoin explorer (bx) can be applied to obtain a data flow picture for what is really going on with extended keys. This requires and understanding of the constituent fields of extended keys and understanding those fields provide inputs for operations that are frequently cascaded in practice, e.g. implementing the BIP 44 Standard using HD wallets.
Each extended key, xprv or xpub, has the following six fields: 1) Version, 2) Depth, 3) Parent Fingerprint, 4) Child Index, 5) Chain Code, 6) Key. The key is either the private or public elliptic curve key depending upon if the extended key starts with xprv or xpub for bitcoin. Note that bx extends the entropy to 12, 15, 18, 21, or 24 triplets of BIP 39 words as a function of the the number of hexadecimal digits cut, using the UNIX cut command. Here is how 12, 18, and 24 BIP 39 seed words are synthesized using bx.
% echo "brain wallets typically have poor entropy" | bx base16-encode | bx sha256
f09538a516514dc74510b08e9d61a0f0200097b4304a88dd96ef613ec3c6f3b3
Now plug the hexadecimal number immediately above into the BIP32 JavaScript program's Input Your own Entropy field, click the Base 16 (0-9,A-F) (For 16-sided dice) radio button, and finally click the Generate New Phrase button. Contrast to the results generated by bx.
% echo "brain wallets typically have poor entropy" | bx base16-encode | bx sha256 | cut -c 1-64 | bx mnemonic-new
vacuum prefer citizen coach below together begin bid model twelve habit theory abandon envelope speak announce match uncover rookie second umbrella toddler solution legal
% echo "brain wallets typically have poor entropy" | bx base16-encode | bx sha256 | cut -c 1-48 | bx mnemonic-new
vacuum prefer citizen coach below together begin bid model twelve habit theory abandon envelope speak announce match tribe
% echo "brain wallets typically have poor entropy" | bx base16-encode | bx sha256 | cut -c 1-32 | bx mnemonic-new
vacuum prefer citizen coach below together begin bid model twelve habit tiger
Notice all the word group sets match to the maximum extent possible except the last word. This is because with BIP 39, the last word of a 12 word sequence has a 4-bit checksum built into it, the last word of a 18 word sequence has a 6-bit checksum built in, and the last word of a 24 word sequence has an 8-bit checksum built in. You can think of the BIP 39 enabling base 2048 encoding with the last word providing checksum information in accordance with the table here.
Now enter the PassPhrase "Hello its me 123!" (typically of your choosing) into the Optional password field and press the enter key. Contrast the results to:
% echo "vacuum prefer citizen coach below together begin bid model twelve habit theory abandon envelope speak announce match uncover rookie second umbrella toddler solution legal" | bx mnemonic-to-seed -p "Hello its me 123!" | bx hd-new -v 76066276
xprv9s21ZrQH143K4R8iufF8sxh3Y5S14mhwn5qLFdi1gymFpr7DWKmMwttkAsLMDYpgJBfNmzTnFUKiveLKZBWzad4A43whiGzWhLtbbwdBQby
Now contrast these six piped bx command line sequences to the six fields created by the BIP 32 JavaScript.
1) Version:
% echo xprv9s21ZrQH143K4R8iufF8sxh3Y5S14mhwn5qLFdi1gymFpr7DWKmMwttkAsLMDYpgJBfNmzTnFUKiveLKZBWzad4A43whiGzWhLtbbwdBQby | bx base58-decode | cut -c 1-8
0488ade4 (where 0x0488ade4 = 76066276 base10)
2) Depth:
% echo xprv9s21ZrQH143K4R8iufF8sxh3Y5S14mhwn5qLFdi1gymFpr7DWKmMwttkAsLMDYpgJBfNmzTnFUKiveLKZBWzad4A43whiGzWhLtbbwdBQby | bx base58-decode | cut -c 9-10
00
3) Parent Fingerprint:
% echo echo xprv9s21ZrQH143K4R8iufF8sxh3Y5S14mhwn5qLFdi1gymFpr7DWKmMwttkAsLMDYpgJBfNmzTnFUKiveLKZBWzad4A43whiGzWhLtbbwdBQby | bx base58-decode | cut -c 11-18
00000000
4) Child Index:
% echo xprv9s21ZrQH143K4R8iufF8sxh3Y5S14mhwn5qLFdi1gymFpr7DWKmMwttkAsLMDYpgJBfNmzTnFUKiveLKZBWzad4A43whiGzWhLtbbwdBQby | bx base58-decode | cut -c 19-26
00000000
5) Chain Code:
% echo xprv9s21ZrQH143K4R8iufF8sxh3Y5S14mhwn5qLFdi1gymFpr7DWKmMwttkAsLMDYpgJBfNmzTnFUKiveLKZBWzad4A43whiGzWhLtbbwdBQby | bx base58-decode | cut -c 27-90
ecdd0dc94d9686e0c5925f0c5657945c370daa9218afae35a75d63ecc9d5c719
6) Private secp256k1 Elliptic Curve Key:
% echo xprv9s21ZrQH143K4R8iufF8sxh3Y5S14mhwn5qLFdi1gymFpr7DWKmMwttkAsLMDYpgJBfNmzTnFUKiveLKZBWzad4A43whiGzWhLtbbwdBQby | bx base58-decode | cut -c 93-156
ee3c1e5f21505c8d1f8ad137fc5a7021f1be309ab1c3cb2bf7e9df80e6521b6f
or
% echo xprv9s21ZrQH143K4R8iufF8sxh3Y5S14mhwn5qLFdi1gymFpr7DWKmMwttkAsLMDYpgJBfNmzTnFUKiveLKZBWzad4A43whiGzWhLtbbwdBQby | bx hd-to-ec
ee3c1e5f21505c8d1f8ad137fc5a7021f1be309ab1c3cb2bf7e9df80e6521b6f
Now for the freekin cascading HMAC-SHA512 mathematical magic for calculating up to 2 to 4 billion public keys and associated public addresses for extended public keys. Note that the following two piped calculations produce identical answers except the means for calculating the results vary, examine carefully. From a business process re-engineering perspective, this is a cryptographic death knell for expensive credit card PCI-DSS customer protection compliance for existing web commerce servers requiring sensitive personal credit card information. Commerce servers accepting crypto don't need to have private keys exposed to process each customers shopping cart's payments.
% echo xprv9s21ZrQH143K4R8iufF8sxh3Y5S14mhwn5qLFdi1gymFpr7DWKmMwttkAsLMDYpgJBfNmzTnFUKiveLKZBWzad4A43whiGzWhLtbbwdBQby | bx hd-private -d -i 44 | bx hd-private -d -i 0 | bx hd-private -d -i 3 | bx hd-private -i 2 | bx hd-public -i 1
xpub6HCiK4CPBLGVw2fJ9bpjHRQ9JwMK2GpcHjszHsvSYZQ6xezqdbiwa2U3QGgKqRdfFNCma9XxXRpaTU2tW9KkgKv6BafobcZmCys5GpZN5QG
or
% echo xprv9s21ZrQH143K4R8iufF8sxh3Y5S14mhwn5qLFdi1gymFpr7DWKmMwttkAsLMDYpgJBfNmzTnFUKiveLKZBWzad4A43whiGzWhLtbbwdBQby | bx hd-private -d -i 44 | bx hd-private -d -i 0 | bx hd-public -d -i 3 | bx hd-public -i 2 | bx hd-public -i 1
xpub6HCiK4CPBLGVw2fJ9bpjHRQ9JwMK2GpcHjszHsvSYZQ6xezqdbiwa2U3QGgKqRdfFNCma9XxXRpaTU2tW9KkgKv6BafobcZmCys5GpZN5QG
Now plug the xpub* extended key immediately above into the BIP32 Extended Key field and press enter and contrast the results to the info below:
1) Version:
% echo xpub6HCiK4CPBLGVw2fJ9bpjHRQ9JwMK2GpcHjszHsvSYZQ6xezqdbiwa2U3QGgKqRdfFNCma9XxXRpaTU2tW9KkgKv6BafobcZmCys5GpZN5QG | bx base58-decode | cut -c 1-8
0488b21e (where 0x0488ade4 = 76066276 base10)
2) Depth:
% echo xpub6HCiK4CPBLGVw2fJ9bpjHRQ9JwMK2GpcHjszHsvSYZQ6xezqdbiwa2U3QGgKqRdfFNCma9XxXRpaTU2tW9KkgKv6BafobcZmCys5GpZN5QG | bx base58-decode | cut -c 9-10
05
3) Parent Fingerprint:
% echo echo xpub6HCiK4CPBLGVw2fJ9bpjHRQ9JwMK2GpcHjszHsvSYZQ6xezqdbiwa2U3QGgKqRdfFNCma9XxXRpaTU2tW9KkgKv6BafobcZmCys5GpZN5QG | bx base58-decode | cut -c 11-18
f32fe933
4) Child Index:
% echo xpub6HCiK4CPBLGVw2fJ9bpjHRQ9JwMK2GpcHjszHsvSYZQ6xezqdbiwa2U3QGgKqRdfFNCma9XxXRpaTU2tW9KkgKv6BafobcZmCys5GpZN5QG | bx base58-decode | cut -c 19-26
00000001
5) Chain Code:
% echo xpub6HCiK4CPBLGVw2fJ9bpjHRQ9JwMK2GpcHjszHsvSYZQ6xezqdbiwa2U3QGgKqRdfFNCma9XxXRpaTU2tW9KkgKv6BafobcZmCys5GpZN5QG | bx base58-decode | cut -c 27-90
fcab24d09be9a54f466c633f24cf76927b90ed2235513d00bc76582e21fdde10
6) Public secp256k1 Elliptic Curve Key:
% echo xpub6HCiK4CPBLGVw2fJ9bpjHRQ9JwMK2GpcHjszHsvSYZQ6xezqdbiwa2U3QGgKqRdfFNCma9XxXRpaTU2tW9KkgKv6BafobcZmCys5GpZN5QG | bx base58-decode | cut -c 91-156
03f800bc151043e197697bf44d90ffa2f9fee3bccc3b49f36f29cee527f3f9af75
or
% echo xpub6HCiK4CPBLGVw2fJ9bpjHRQ9JwMK2GpcHjszHsvSYZQ6xezqdbiwa2U3QGgKqRdfFNCma9XxXRpaTU2tW9KkgKv6BafobcZmCys5GpZN5QG | bx hd-to-ec
03f800bc151043e197697bf44d90ffa2f9fee3bccc3b49f36f29cee527f3f9af75
Calculation of associated M/44'/0'/3'/2/1 compressed public address:
% echo xpub6HCiK4CPBLGVw2fJ9bpjHRQ9JwMK2GpcHjszHsvSYZQ6xezqdbiwa2U3QGgKqRdfFNCma9XxXRpaTU2tW9KkgKv6BafobcZmCys5GpZN5QG | bx hd-to-ec | bx ec-to-address -v 0
1HaigDWQCAu3eJQnKivhVifcrcQDEYdDBH
Calculation of associated m/44'/0'/3'/2/1 compressed WIF key:
% echo xprv9s21ZrQH143K4R8iufF8sxh3Y5S14mhwn5qLFdi1gymFpr7DWKmMwttkAsLMDYpgJBfNmzTnFUKiveLKZBWzad4A43whiGzWhLtbbwdBQby | bx hd-private -d -i 44 | bx hd-private -d -i 0 | bx hd-private -d -i 3 | bx hd-private -i 2 | bx hd-private -i 1 | bx hd-to-ec | sed 's/$/01/' | bx base58check-encode -v 128
KzNMg2qRVNBbr2QnAzc2bYvf7cM2t4GQ2LiL1Q5VYgWipTrrPKbX
- 3,017
- 1
- 12
- 23
-
thank you for such a thorough answer and demonstration, I wish you good health – Phạm Huy Phát Aug 16 '18 at 02:50