I have a brand new Active Directory (CORP-AD) installation running on Windows 2008R2. I have a domain controller (PDC01) and a member server (ME01).
The member server has a C: and a D: drive.
Part of our standard build is to remove all permissions from the root of the D: drive except for:
SYSTEM (Full Control) Administrators (Full Control)
I created a new domain user ADMIN01 and granted it membership of the Domain Admins group.
Domain Admins is a member of the member server's local Administrators group.
When I logon (via RDP) to the member server ME01 as the domain user ADMIN01 this user cannot access the D: drive. I then tried adding the Domain Admins group with full control to the root of the D: drive but my ADMIN01 user still cannot access the D: drive:
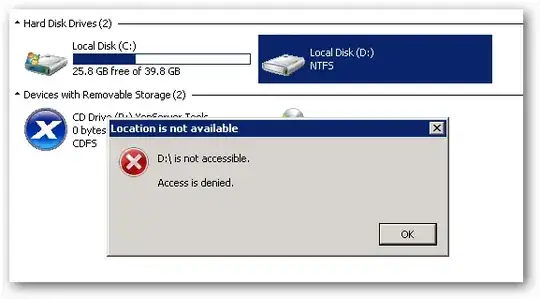
If I logon to ME01 as a local machine administrator I have no trouble accessing the D: drive at all.
I discovered this question which describes more or less the same problem:
Why can't I browse my D: drive, even if I'm in the Administrators group?
The answer suggests correctly that this is a UAC privilege elevation issue but I'm puzzled by this statement, in particular the bold part:
You can modify this behaviour by Group Policy however bear in mind that the default is set that way intentionally - the specific policy you want to change is "User Account Control: Run all administrators in Admin Approval Mode" - you can find details on how to do this in this MSDN article.
Is this suggesting that "User Account Control: Run all administrators in Admin Approval Mode" should not be disabled?
If it's enabled I don't get a UAC challenge with the "Continue" button + shield icon, I'm just plain refused access to the drive. Is this normal?