The recommended way of securely erasing a SSD is the ATA secure erase. Most of the BIOSes disable this function by freezing the drive. Some tricks around the BIOS freeze exist and may or may not work depending on the setup. This makes ATA secure erase difficult to use.
Could triming be misused as an alternative to securely erasing a SSD?
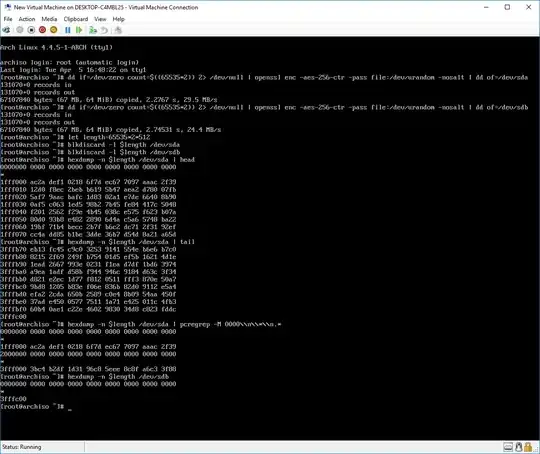
One could delete any existing partition table and create a new GPT with one ext4 partition filling the whole SSD. Triming the ext4 partition would cause the SSD to erase all logical blocks on the SSD but the blocks holding the GPT and the ext4 super block. Reserve blocks which are not assigned to a logical block are erased by definition. This way all physical blocks would either be erased or contain useless GPT/ext4 meta information.
Do you see any flaw in this plan?
Please do not answer that ATA secure erase should be used to securely erase a SSD, this is not the question.