(final) update: Dear friends, Dell support has transferred me to the dev team. They say its a bug. Too soon to tell if its fatal, but if I don's survive I want the bounty to go to .... ughhh
I'm attempting to add users on the SonicWALL from a Windows AD. I want the windows logon password to be the VPN password through the SonicWALL VPN functionality.
From Users > Local users > import from ldap > I pick the user and it creates it. However, I keep getting the below error:
Warning: Password is too short (new password has not been saved, please try again)
In the SonicWALL configurations the password policy options were set to 8 length, 1 upper, 1 lower, 1 number. I've since turned the password complexity requirements off within system > administration, set the password to a simple 8 character password with no special characters ("Qwerty12"), and I even recreated the user account but I still have the same issue.
The SonicWALL logs show the user account being created, but it doesn't show anything about the password at all when the issue arises that I see.
I'm not sure why it won't take a password as it should be perfectly valid complexity and special character wise, and typed in correctly too.
Other Detail
SonicWALL support spent an hour recreating my issue and they've been "researching" further for 2 days now supposedly.
My firmware has been updated to the latest.
- SonicOS Enhanced 5.9.1.6-5o
I am not using a RADIUS server.
I'm seeing the below warning message as well when I click some screens.
Note that LDAP authentication is selected with Active Directory, and it does not support CHAP authentication via LDAP. If L2TP users are to use CHAP then you should configure RADIUS so that it can be used for this, if you have not already done so.
My remote end-users are NOT using CHAP. I'm not sure if this in anyway applies to the SonicWALL <--> Active Directory LDAP communication.
The VPN connection works if I manually change the password.
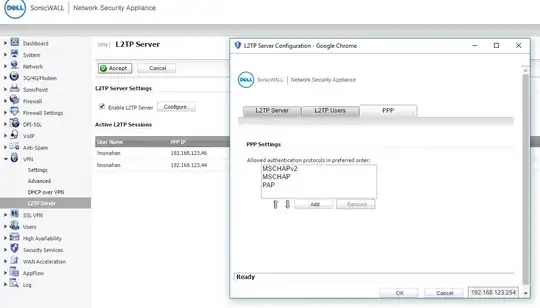
See print screen below labeled as L2TP Server Configuration for what's set there but behind that windows it shows that I'm connected with MS-CHAP V2.
I also changed the schema to use full bind distinguished name so it's
<Username>@<domain.com>and the LDAP test was successful still after re-importing the account but I still have the same issue otherwise.Below is a print screen of the LDAP Test Results which is successful. My admin account can be read from LDAP as can the user tester2 both successfully.