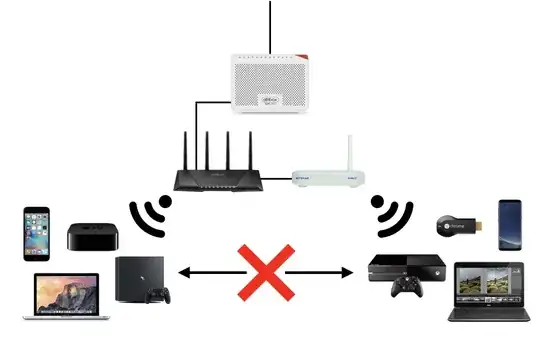
A huge amount depends on the exact hardware you have, how its connected, and your networking confidence. Can you add a list of exact models of the 3 items of WiFi and routing equipment in your picture, including the actual box connecting you to the internet if its different (pictures arent any use) and a bit of description of your confidence, experience or ability, to the question?
Also importantly, we need to know more exact details for how the networking should end up. Are all connections WiFi or are any devices connected using network cables, if so which? How many devices are connected in total, which are connected to which, and how are they connected (WiFi/wired)? Which ones must be able to talk with each other, or blocked from seeing each other?
Its quite a bit of info but if you can add it, someone might be able to answer you and help.
As it stands, a good answer for you could be anything from "Its built-in, do it this way", through to "install OpenWRT because the manufacturer code doesn't allow it", thorough to complete noob help or reorganising it all. What I do here is a different solution again - add a software router I've installed myself, to control access. So you can see, there are several options depending on you and your equipment. But what you're after should not be difficult to do, for almost any router, even a home router.
The basic answers are adding firewall or routing rules (so the two IPs can't communicate), using built-in isolation if included, or using VLANs. The first two are usually easiest if its new to you. Not all home routers have the second. Almost all home routers have enough capability to do this using rules and/or routing. In many cases it depends on which exact devices on the network need to be able to see (or not see) which other devices, and how they are connected.
Exact details beyond that are almost impossible without knowing the info above. If you add that, it will be easier to comment.
Update 1: security/privacy
- Bear in mind that if one router's data travels through the other router, the master router is being trusted to not watch its data in transit. Even if the two networks don't communicate, the router that both travel through can see all data, so anyone who controls that device, can arrange to see all data. Is that acceptable?
Update 1: howto
The Asus RT-AC87U is a very nicely featured modern router that beyond doubt will do what you need without thinking twice. The manual (online at Asus support) suggests immediately a number of ways to do it. Two of them look very easy. Other methods would need a bit more explanation and no point to writing on that, if either of the first 2 works well enough.
- Section 3.2 "Creating a guest network" - creates a guest network that can't access your main network, directly on the Asus. Pros - looks dead simple, less to go wrong, and should do what you want. Cons - person using slave router won't have a slave router as it won't be needed, they would connect directly to the Asus which would handle isolation itself. This is by far the easiest way if acceptable.
- The zyxel might be locked down, but it's probably working fine in bridging mode. Even if the ISP has put tape across it other ports, as some do, they should still be bridged if usable. I can't think why they wouldn't be left that way. As the Zyxel almost certainly has its DHCP setup working (we know this because it acts as a router not just a modem), it will handle devices attached via the two other routers. So if you can, try to connect both the Asus and the Netgear directly to it, and see if they can both see the internet at the same time. If they can, its all pretty much solved. What this does is make the Netgear appear to the Asus as a WAN (non local) device, which can be easily blocked 100% and treated as untrustworthy. (It also makes the Asus appear to be on the WAN from the Netgear's perspective but that's not an issue as you explained). You will need to sort out DHCP but as the ISP supply the Zyxel, its quite likely that is already set up properly and will work automatically. What should happen is that the Asus and Netgear (and devices connected to them) will both accept IP addresses from the Zyxel, since you already seem to have the Asus behind the Zyxel anyway, and then set up the network services or firewall or incoming rules, to prevent unexpected packets from outside the Asus passing through the Asus. Pros- all, if it works (which it should). Cons - none if it works (which it should :) )
Try to get one of those two ways working. If you need more help, update your question to explain whay youve tried, what worked and what isnt (yet) working.
See also
- section 4.1.6 "professional" covers the "AP isolation" setting which probably isn't what you want, but is worth knowing about in case it becomes relevant. It would stop all wireless devices connected to the Asus from intercommunicating.
- section 4.6.4 "network services" which covers part of the firewall. It says "blocks LAN to WAN" but there's a chance it could also be used to block LAN to/from WiFi using an IP based rule, and if both routers work behind the zyxel then its probably what you need to lock down incoming packets from the netgear.
Also if confident, don't overlook the option to define a specific IP range (subnet) for devices attached to the Asus, or to use the DHCP server built into it, which will help as well, by ensuring your "master" devices are on a different subnet entirely from the others. See sections 3.1.1 "setting up the wireless security settings" and 4.2.2 covers network setup for the wired network.