Recently we were alerted by an incident on Microsoft Defender titled "Multi-stage incident involving Execution & Discovery on one endpoint" and amongst the commands that ran was a suspcious tool "Healthy.exe"
These are some of the reported commands:
Healthy.exe --type=crashpad-handler "--user-data-dir=C:\Users\DG\AppData\Local\Healthy\User Data" /prefetch:7 --monitor-self --monitor-self-argument=--type=crashpad-handler "--monitor-self-argument=--user-data-dir=C:\Users\DG\AppData\Local\Healthy\User Data" --monitor-self-argument=/prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\DG\AppData\Local\Healthy\User Data\Crashpad" "--metrics-dir=C:\Users\DG\AppData\Local\Healthy\User Data" --annotation=plat=Win64 --annotation=prod=Healthy --annotation=ver=0.0.2 --initial-client-data=0x25c,0x260,0x264,0x258,0x268,0x7ffac8359ec0,0x7ffac8359ed0,0x7ffac8359ee0
"Healthy.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1672,13707566958700461977,3626767176628270657,131072 --lang=en-US --service-sandbox-type=none --no-sandbox --enable-audio-service-sandbox --user-data-dir="C:\Users\DG\AppData\Local\Healthy\User Data" --nwapp-path="C:\Users\DG~1\AppData\Local\Temp\nw12476_1097854171" --mojo-platform-channel-handle=3616 /prefetch:8
The only results I get when searching about it are about "Health exe", which i dont think are the same?
The user ran an AV scan which reported no maliciousness so not sure if this is still worrisome or not.
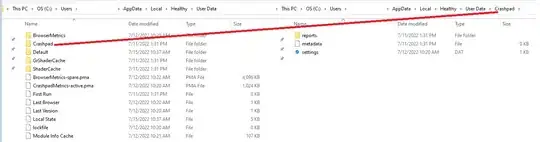
Here are some screenshots from that path specified in the commands:
virus total analysis: