Recently when running a Remote Desktop Connection under this Windows version
OS Name Microsoft Windows 11 Pro
Version 10.0.22621 Build 22621
Other OS Description Not Available
OS Manufacturer Microsoft Corporation
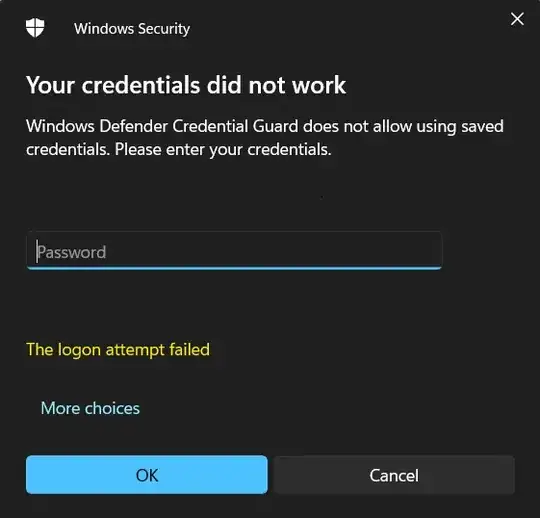
I can no longer use the saved RDP credentials and every connection gives this message:
Upon google'ing, I've tried editing registry values, policy changes, rebooting etc.,... but nothing is working.
I'd like to use Remote Desktop without having to manually enter my credentials each time!
Any ideas?