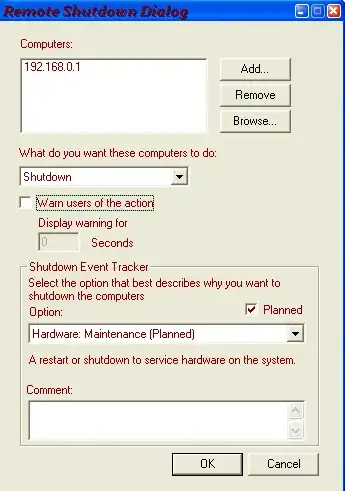
The policy you want to change is in
Computer Configuration | Windows Settings | Security Settings | Local Policies | User Rights Assignment
Locate the policy named "Force shutdown from a remote system." By default, this policy has a value of Administrators. Just edit it to be an empty list, or put your friendly trusted IT person in there instead.
A note about "Shutdown: Allow system to be shut down without having to log on"
This policy applies to local shutdowns only. That is, it controls whether someone present at the computer can shut it down without having to log on first. By default, this policy is Enabled on workstations, and you can see the shutdown button in the lower right corner of the Windows logon screen.

If you set this policy to Disabled, you will no longer see the shutdown button on the logon screen. A user would have to log on to the computer to shut it down. This is typically how servers are setup.

This policy does nothing to prevent a remote shutdown. You can try it yourself on a system that you can shutdown remotely. Set this policy to Disabled, and you will still be able to shut down that system.
A note about the Remote Registry service
Disabling the Remote Registry service does not prevent remote shutdowns. Remote Registry only affects the ability of the Shutdown Event Tracker to record the reason for the shutdown. If the reason cannot be recorded, the shutdown still occurs.