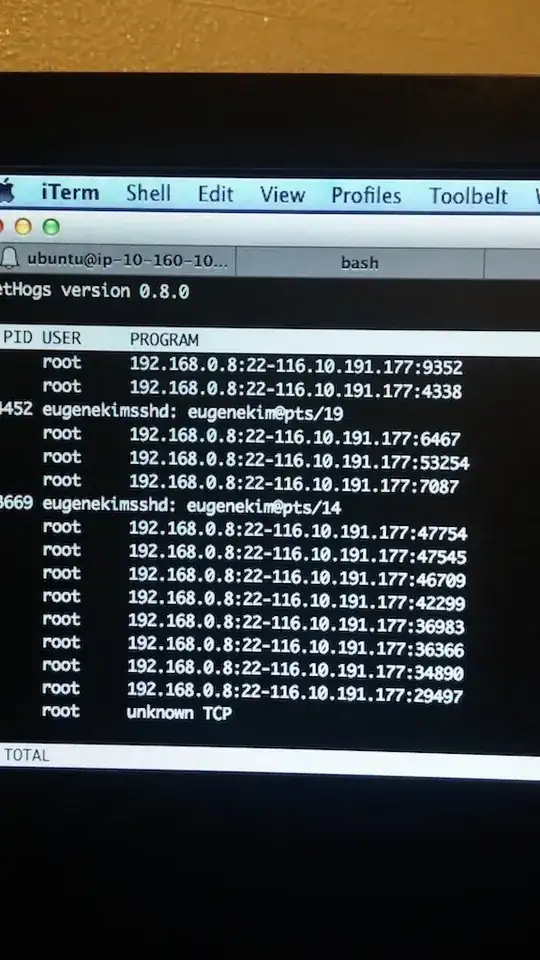
My home network is frequently down and I've narrowed down the problem to my ubuntu box.
$ ps -ef | grep elastic
elastic+ 11183 1 0 8월10 ? 00:07:49 [.ECC6DFE919A382]
eugenek+ 14482 14453 0 22:08 pts/19 00:00:00 grep elastic
elastic+ 20208 1 0 8월07 ? 00:01:35 [.......]
elastic+ 24398 1 0 8월08 ? 00:01:20 [SSHD]
elastic+ 24745 1 4 10:44 ? 00:27:29 /tmp/.Udelo
elastic+ 27895 1 0 8월09 ? 00:00:47 [.......]
elastic+ 28652 1 0 8월09 ? 00:00:46 [.......]
elastic+ 31127 1 0 8월09 ? 00:00:41 [.......]
elastic+ 31223 1 0 8월07 ? 00:01:34 [.......]
elastic+ 31460 1 0 19:23 ? 00:00:02 [freeBSD]
elastic+ is elasticsearch user which is created when I set up the elasticsearch server.
Does it look strange? or are they regular processes run by elasticsearch?
EDIT
I also found this.. So it looks severe than what kmac originally suggested?
116.10.191.177 is not someone I know, it's from China..